How it Works
OwnID supports integration with Okta through our pre-built Okta Connector. Configuration on the Okta side happens through your Okta Admin Dashboard. Ensure you have an account with admin access in Okta. Complete these five basic steps to integrate OwnID with Okta: Step 1 - Extend Okta User Schema. Step 2 - Create Okta API Token. Step 3 - Create the OwnID App. Step 4 - Create an Identity Provider. Step 5 - Frontend Integration.Step 1 - Extend Okta User Schema
Add an attribute in Okta calledownIdData. This is used to store user authentication data in Okta.
- In your Okta Admin Dashboard go to Directory -> Profile Editor.
-
Select the User (default) user group.
 Figure 1. Profile editor
Figure 1. Profile editor
-
Click +Add Attribute.
 Figure 2. Add attribute
Figure 2. Add attribute
-
Complete the attribute configuration as shown below.
 Figure 3. Attribute configuration
Figure 3. Attribute configuration
- Click Save.
Securing User’s Personal DataOwnID does not store or process any user data. Users’ public keys and device information are stored on your platform.Private keys are kept exclusively on the user’s device and are never transmitted elsewhere.
Step 2 - Create Okta API Token
- In your Okta Admin Dashboard, go to: Security -> API -> Tokens tab.
-
Click Create Token.
 Figure 4. Create API token
Figure 4. Create API token
- Fill in the token name - “OwnID API Token”.
-
Copy the token value. We will use it in the next step.
 Figure 5. Copy API token
Figure 5. Copy API token
- Click OK, got it after copying the token.
Step 3 - Create the OwnID App
We’ll create a new OwnID app using the Okta Connector.

appId automatically. Use that appId in OwnID SDK interaction from your website’s front end.
To Create an OwnID App
- Login to the OwnID Console (or create your account).
- Click +Create Application from the Apps screen.
- Enter a name for your application in the App name field.
-
From the Choose your integration panel, select the Okta tile.

- Click Next.
-
Click Explore my App on the “Congratulations” popup.

Set Okta Integration Parameters
In your Okta integration page, fill in the following information:- In Okta Settings, set the Site Domain - e.g: https://acme.okta.com
- In Okta Settings, set the API Token value you created above.
-
In Okta Settings, skip the Identity Provider ID for now. We will get this in a later step.

-
In OpenID Connect settings, set Redirect URIs by adding one or more Okta redirect URIs, typically in the format
https://your-auth-domain.com/oauth2/v1/authorize/callback.
- Click Save Changes.
Step 4 - Create an Identity Provider
Create an OwnID OIDC Identity Provider.- In your Okta Admin Dashboard, go to Security -> Identity providers.
-
Click Add identity provider.
 Figure 6. Add identity provider
Figure 6. Add identity provider
-
From the provider options, select the OpenID Connect IdP tile.
 Figure 7. OpenID Connect IdP
Figure 7. OpenID Connect IdP
-
The General settings form opens. Configure it with the following general settings:
 Figure 8. IdP settings
Figure 8. IdP settings
-
For the Client details values use the
Client IDandClient Secretfrom the OwnID application created in the previous step as shown. Figure 9. Client details
Figure 9. Client details
- In Endpoints, enter the values from the OwnID application created in the previous step?
-
Set the remaining details as shown below:
 Figure 10. Authentication settings
Figure 10. Authentication settings
- Click Save.
IdP ID value from the Summary_ so we can use it in the next step.  Figure 11. IdP Summary
Figure 11. IdP Summary
Step 5 - Frontend Integration
- In your Okta Admin Dashboard, go to Customizations -> Brands.
- Select your relevant brand.
-
Click Customize on the Sign-in page panel.
 Figure 12. Brand customization in Okta
Figure 12. Brand customization in Okta
-
Ensure the Code Editor option is toggled on (requires a custom domain).
 Figure 13. Code editor
Figure 13. Code editor
-
Under the
<body>tag, locate the{{{OktaUtil}}}definition, then add the OwnID script for loading the OwnID WebSDK below theOktaUtilline. The script could be fetched from the integration settings of the app in the OwnID Console. Once you fill in the Identity Provider ID created in the previous step, you will have a full snippet ready to copy.
The script could be fetched from the integration settings of the app in the OwnID Console. Once you fill in the Identity Provider ID created in the previous step, you will have a full snippet ready to copy.
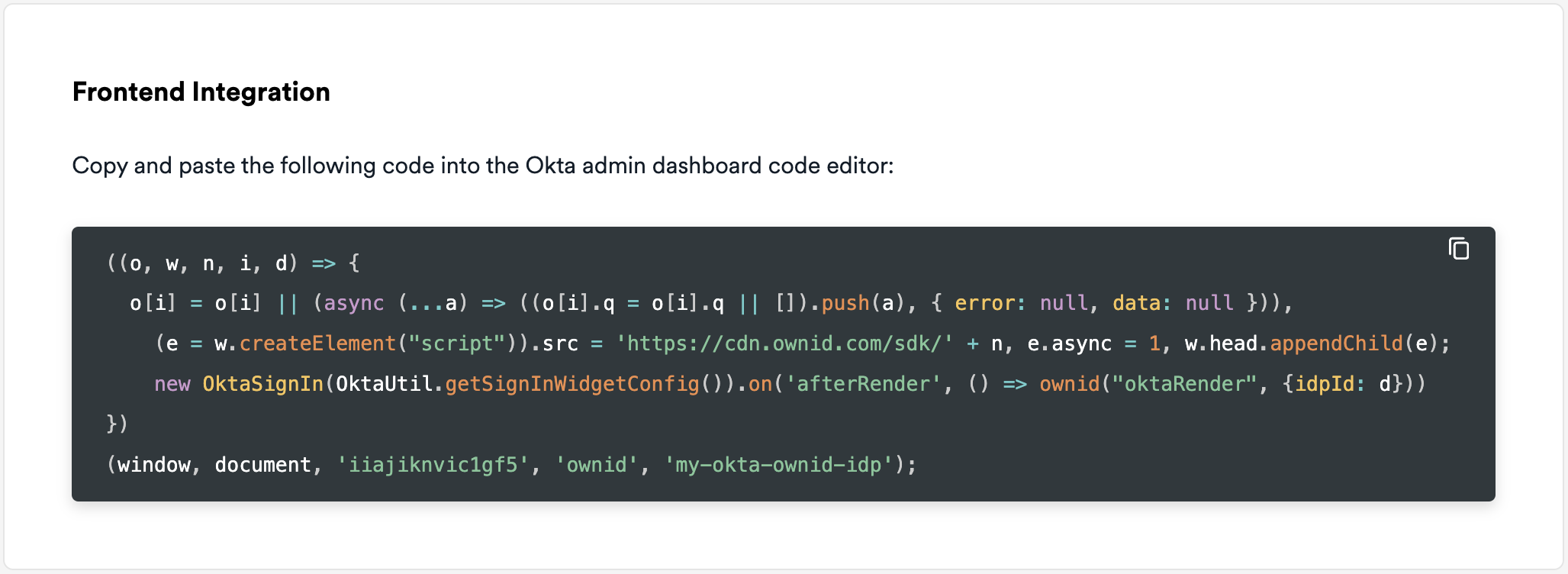
-
Replace
<appId>with theappIdfrom the OwnID application created in step 3. -
Replace
<idpId>with theIdP IDfrom step 4.
-
Replace
Web SDK Configuration
- Click Save and Publish.
Congratulations!
Enjoy your Okta-integrated passwordless authentication!
Enjoy your Okta-integrated passwordless authentication!
Next Steps
Ready to deploy?
YES!
Take me to the Deployment Checklist