How it works
OwnID integrates with the SFCC built-in API client, using our native SFCC Connector. Integrate OwnID with your PWA by completing these four basic steps: Step 1 - Configure OIDC in OwnID Console. Step 2 - Configure SLAS IDP. Step 3 - Configure SFCC permissions. Step 4 - Configure OwnID UI in your app.Prerequisites
- Complete the Salesforce Commerce Cloud (SFCC) integration.
- Have permissions to access and modify SFCC SLAS Admin UI.
- Get a hold of your SFCC instance’s shortcode. It is available from the Business Manager SFCC dashboard, under
Administration > Site Development > Salesforce Commerce API Settings. Its value is typicallykv7kzm78.
Step 1 - Configure OIDC in OwnID Console
- Open the Salesforce integration page in the OwnID Console.
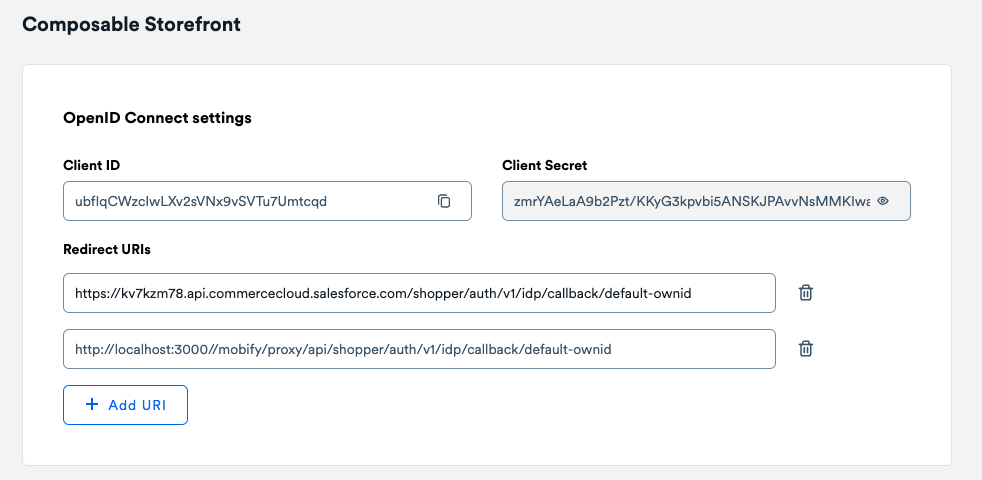
- Scroll down to the OpenID Connect settings section.
- Copy the Client ID and Client Secret values. We will use them in the next step.
- In the Redirect URIs field, add the value
{shortcode} is your SFCC instance’s shortcode. The name default-ownid is the default IDP name. If you have wish to setup a different IDP name, use that instead.
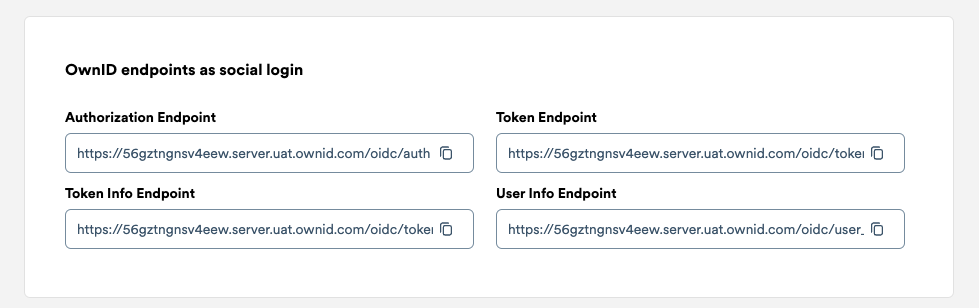
- Copy the endpoints listed in the Endpoints section. We will use them in the next step.
Step 2 - Configure SLAS IDP
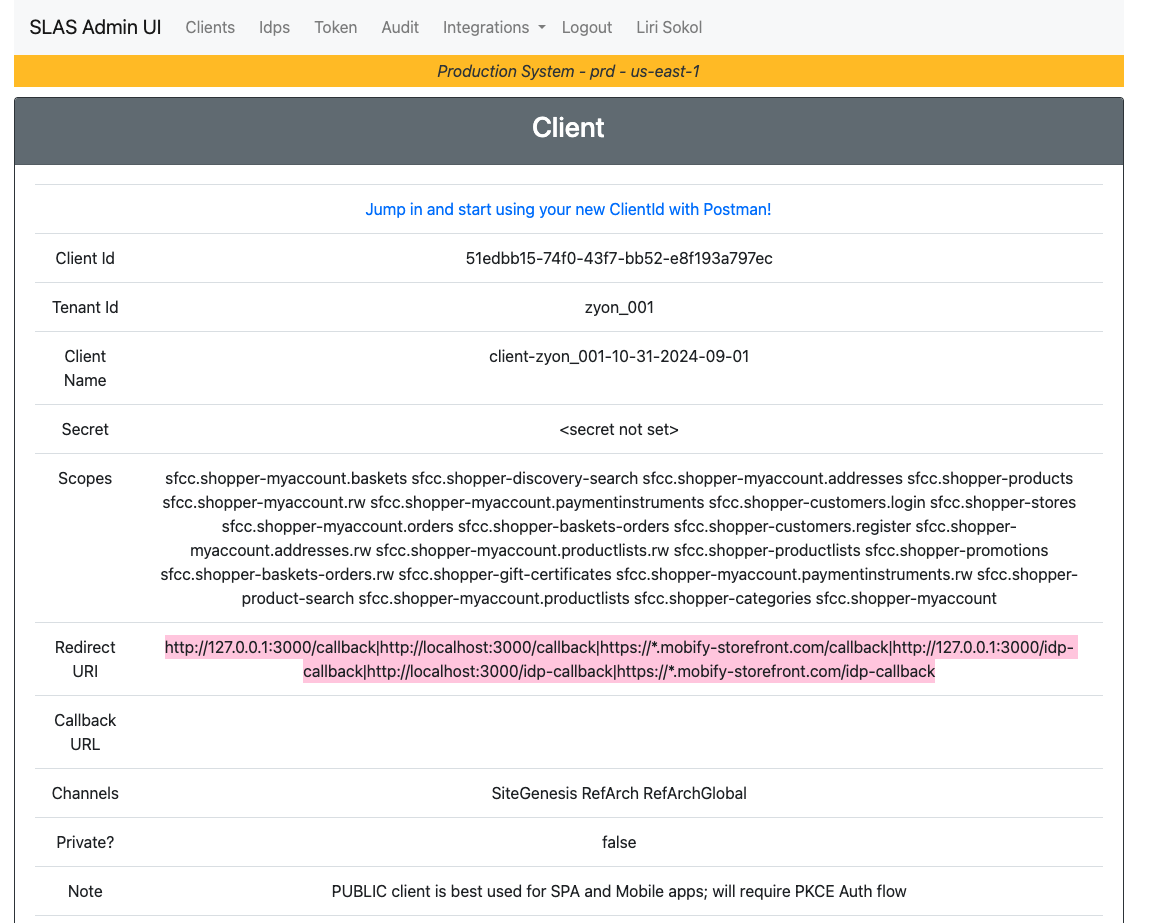
- Open the SFCC SLAS Admin UI, accessible at
https://{shortcode}.api.commercecloud.salesforce.com. - In the Clients tab, edit the redirect URI of the clients you are using in your PWA. Add the endpoint
/idp-callbackfor all relevant domains. Keep the/callbackin place. You can use a different endpoint if you wish, we will configure its value in the PWA in the next step. Just make sure to create a different endpoint than/callback, because this one is used by other authentication flows of SLAS. Value for example:
- Go to the Idps tab and click the Add Idp button.
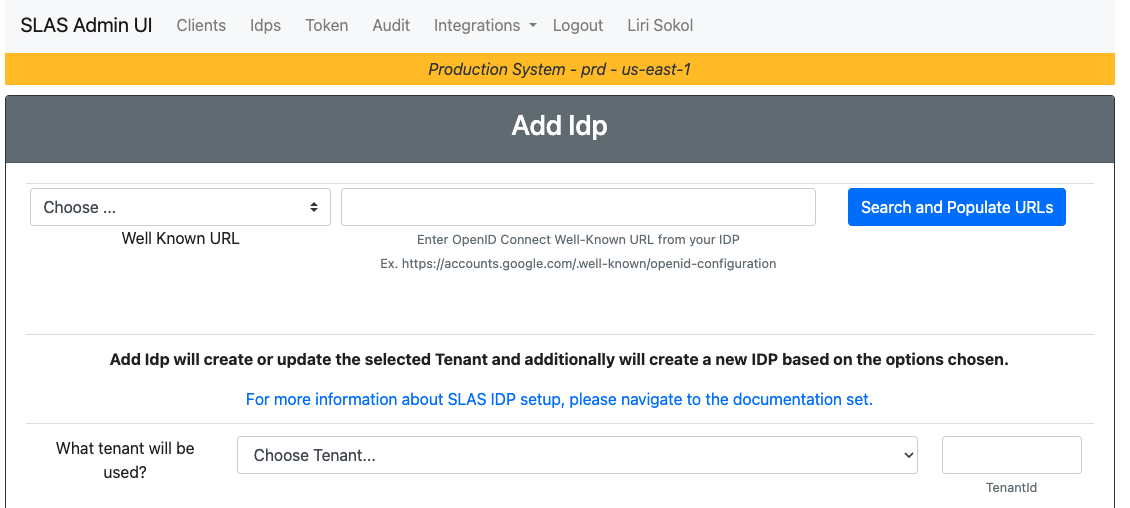
- Fill in the form with the following values:
What tenant will be used?- Choose your tenant.Idp Name- Enterdefault-ownidor the name you used in the OwnID Console.Idp Client Id- Enter the Client ID from the OwnID Console.Secret- Enter the Client Secret from the OwnID Console.Scopes- Enteropenid profile email.Redirect URL- Enterhttps://{shortcode}.api.commercecloud.salesforce.com/shopper/auth/v1/idp/callback/default-ownid, the value you had set in the Redirect URIs field in the OwnID Console.Auth URL- Enter the Authorization Endpoint from the OwnID Console.Token URL- Enter the Token Endpoint from the OwnID Console.Token Info URL- Enter the Token Info Endpoint from the OwnID Console.User Info URL- Enter the User Info Endpoint from the OwnID Console.Well Known URL- Leave empty.Client Credentials in POST body?- check the checkbox.Default IDP Claim Map- Leave empty.Login Merge Claims- Enter the valueemail.Team Id- Leave empty.Key Id- Leave empty.
- Click Submit.
- Go back to the client you are using and copy the Client Id, we will use it in the next step.
Step 3 - Configure SFCC permissions
- Open the SFCC Business Manager.
- Go to Administration > Site Development > Open Commerce API Settings.
- Add the following JSON object to the shop tab:
shop tab
Client ID with the Client Id from the SLAS Admin UI.
Step 4 - Configure OwnID UI in your app
- Open your PWA project in your IDE. First install the OwnID React SDK:
npm react
- Edit
ssr.js(typically atoverrides/app/ssr.js) and add'*.ownid.com'to bothscript-srcandconnect-srcCSP headers. - Import and configure the OwnIDInit component. Make sure to include so that it is rendered either on every page or on every page relevant to authentication flows.
In the the
appIdfield, use the app ID from the OwnID Console. In theidpNamefield, use the name you used in the SLAS IDP configuration, by default it isdefault-ownid. In thecallbackEndpointfield, use the endpoint you configured in the SLAS client redirect URI. We recommend on/idp-callback.
OwnIDInit
- Customize the login form to include the OwnID widget. By default you would need to override
app/components/forms/login-fields.jsx.
overrides/app/components/forms/login-fields.jsx
- Customize the registration form to include the OwnID widget. By default you would need to override
app/components/forms/registration-fields.jsx.
overrides/app/components/forms/registration-fields.jsx
- Add a new dedicated page to handle the OAuth callback. This is the route that we will map to
/idp-callback. Typically, it would be atpages/idp-callback/index.jsx. The UI in the snippet is only a recommendation, you can customize it to fit your needs. The important bits are the call towindow.ownid.completeAuthorizeFlowand the handling of theusidandcodequery parameters. In addition, make sure to handle an already authenticated user in already to avoid a redirect loop. This is done in the snippet using theuseCurrentCustomerhook.
overrides/app/pages/idp-callback/index.jsx
- Add a handler in your account page (typically
pages/account/index.jsx) to handle post-registration flow.
overrides/app/pages/account/index.jsx