How it Works
OwnID integrates with the SFCC built-in API client, using our native SFCC Connector and an SFCC cartridge. Integrate OwnID with SFCC by completing these four basic steps: Step 1 - Get SFCC Credentials. Step 2 - Create an OwnID application in the OwnID Console. Step 3 - Install the SFCC Cartridge. Step 4 - Add OwnID SDK script to your template.Prerequisites
- Download the Salesforce Commerce Cloud cartridge here.
- Have permissions to access and modify SFCC Account Manager and SFCC instance’s Administration.
Step 1 - Add SFCC Client
Integration requires you to create a new API Client in your SFCC instance.Create Credentials
See: Add an API Client in B2C Commerce- Log into the SFCC Account Manager.
- Select API Client from the left side menu.
- Click Add API Client.
- Enter “OwnID Integration” in Display Name.
- Enter a password.
- Assign your organization.
- Assign the following roles:
Sandbox API UserSalesforce Commerce Cloud
- In the Token Endpoint Auth Method, select
private_key_jwt. - Click Save Changes.
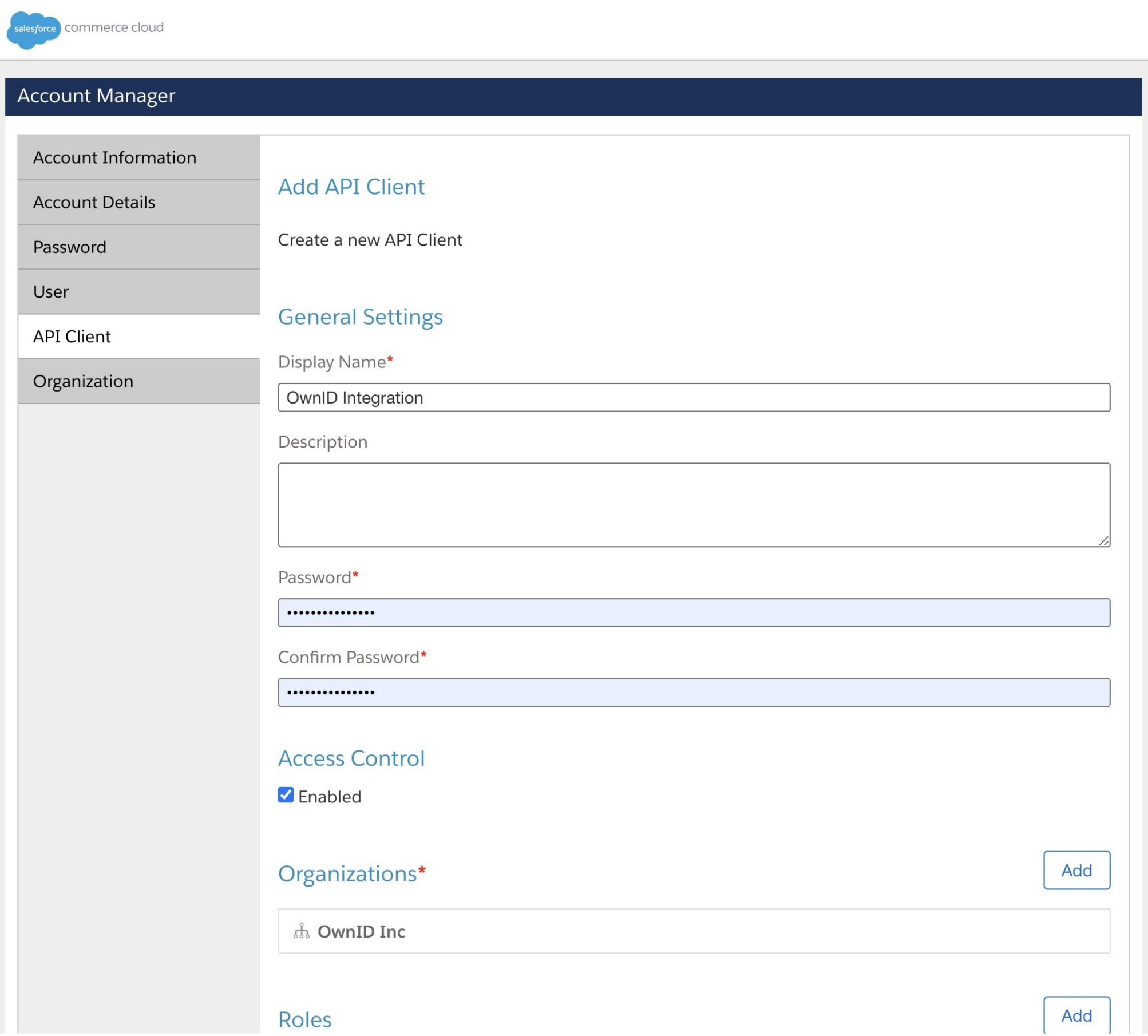
Client Id and Secret. Save these values for later use.
Assign Permissions
- Go to Administration > Site Development > Open Commerce API Settings.
-
Add the following JSON object to the shop tab. Change
client_idvalue in the following shop JSON to match theClient Idcreated in the previous steps.
shop tab
- Add the following JSON object to the data tab. Change
client_idvalue in the following data JSON to match theClient Idcreated in the previous steps.
data tab
Securing User’s Personal DataOwnID does not store or process any user data. Users’ public keys and device information are stored on your platform.Private keys are kept exclusively on the user’s device and are never transmitted elsewhere.
Step 2 - Create OwnID Application
An OwnID App is what connects the existing identity provider used by your website with the OwnID widget you insert on the front end.
appId automatically. Use that appId in OwnID SDK interaction from your website’s front end.
To Create an OwnID App
- Login to the OwnID Console (or create your account).
- Click +Create Application from the Apps screen.
- Enter a name for your application in the App name field.
-
From the Choose your integration panel, select the tile.

- Click Next.
- Enter the website URL to your application instance and click Continue.
-
Click Explore my App on the “Congratulations” popup.

-
From the OwnID Settings panel, copy the App ID and the Shared Secret for use in configuration on the side.

Your OwnID application and secret key are created and you’re ready for next steps!
Salesforce Commerce Integration Configuration
- Open the Salesforce integration page in the OwnID Console.
- Enter the Instance Hostname - e.g: xyzb-001.dx.commercecloud.salesforce.com (only the domain, without protocol).
- Enter a Site ID - e.g: RefArch (case sensitive).
- Enter the API Client ID (generated in the previous step).
- Enter the API Client Secret (generated in the previous step).
- Enter the SFCC Username (get it from the Account Manager).
- Enter the SFCC Password.
- Click Save Changes.
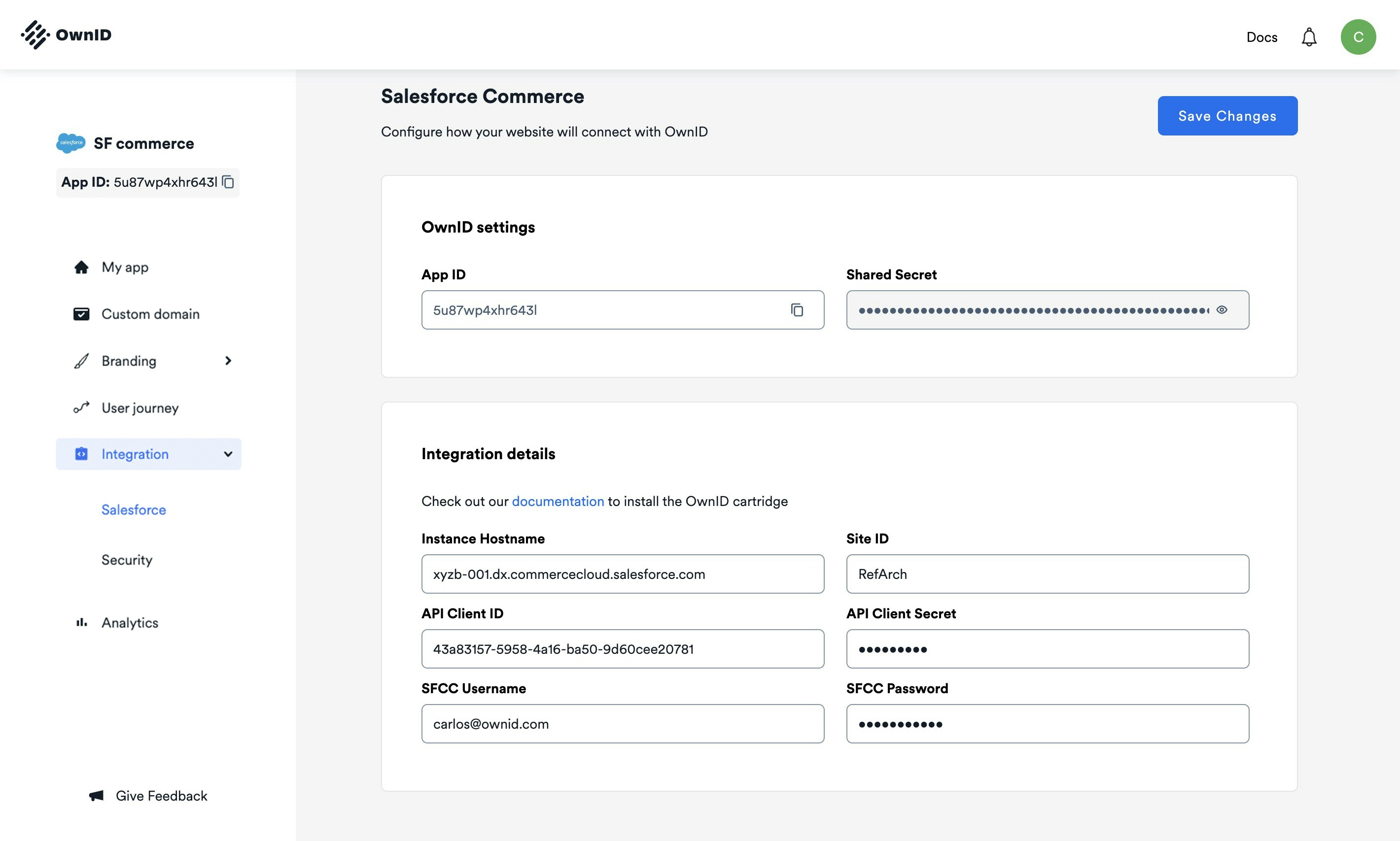
appId so you can use it in the next step.
Security Configuration
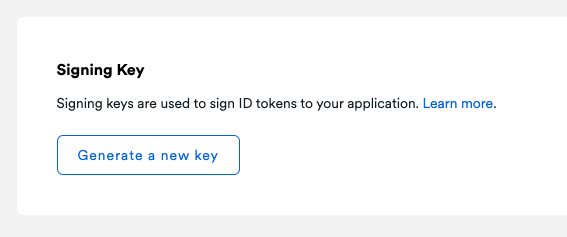
- Go to Integration > Security
- On the Signing Key panel, click Generate a new key
- Save this key so you can use it in the next step.
Step 3 - Install the SFCC Cartridge
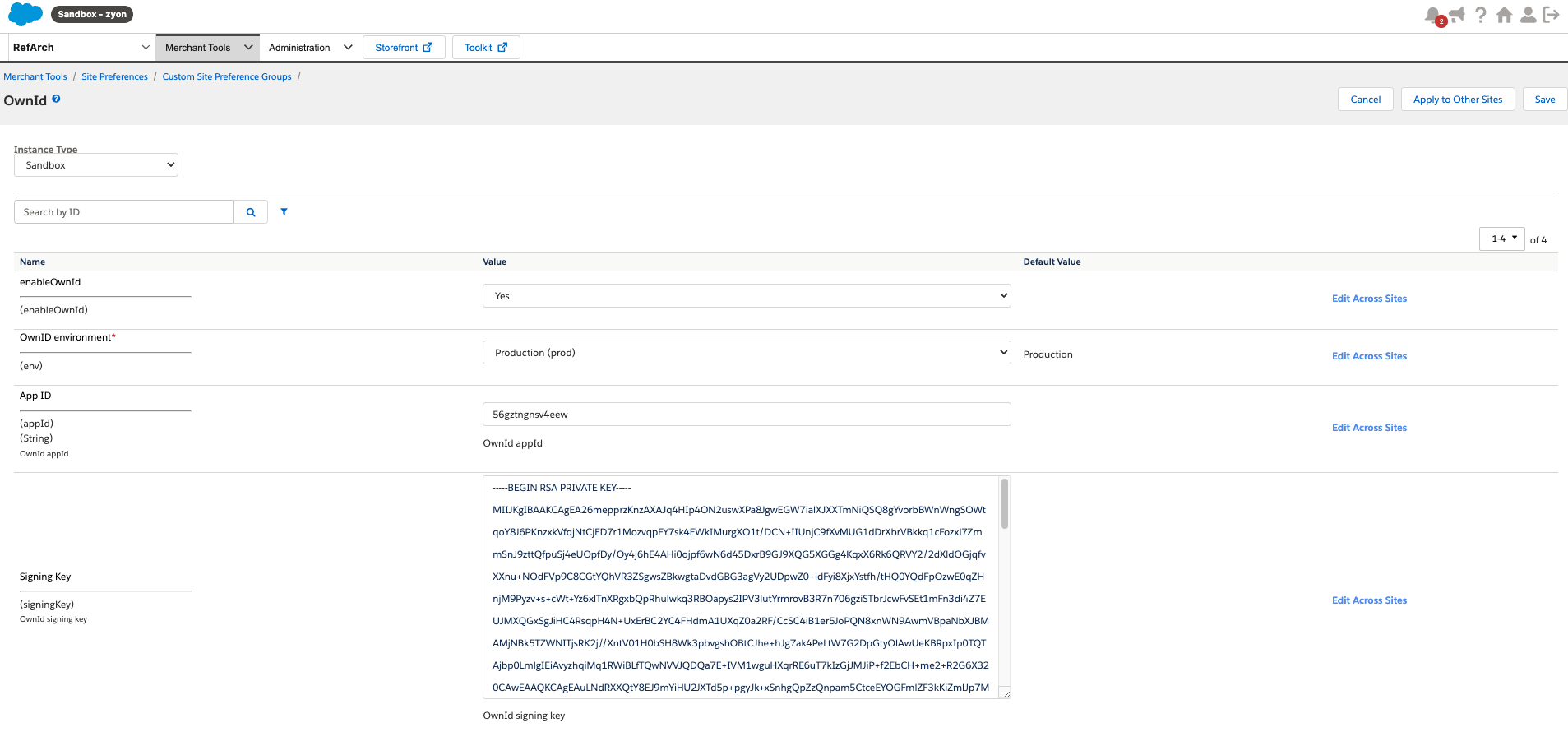
- Upload and add the cartridge to the target site.
- Navigate to Merchant Tools > Site Preferences > Custom Preferences > OwnID and set the following preferences:
- Set
EnableOwnIdtotrueto display the OwnID widget. EnvSelect the OwnID production environment.- Enter the
AppIdpreviously copied from the OwnID Console. - Enter the
Signing Keypreviously copied from the OwnID Console.
Step 4 - Add OwnID SDK script to your template
After the cartridge is installed, you need to add this script to a template that is rendered in all pages, such astemplates/default/common/htmlHead.isml
Make sure the script is added to all the pages of your website
Advanced Configuration
Styling Options
Default Button (Side-by-side)
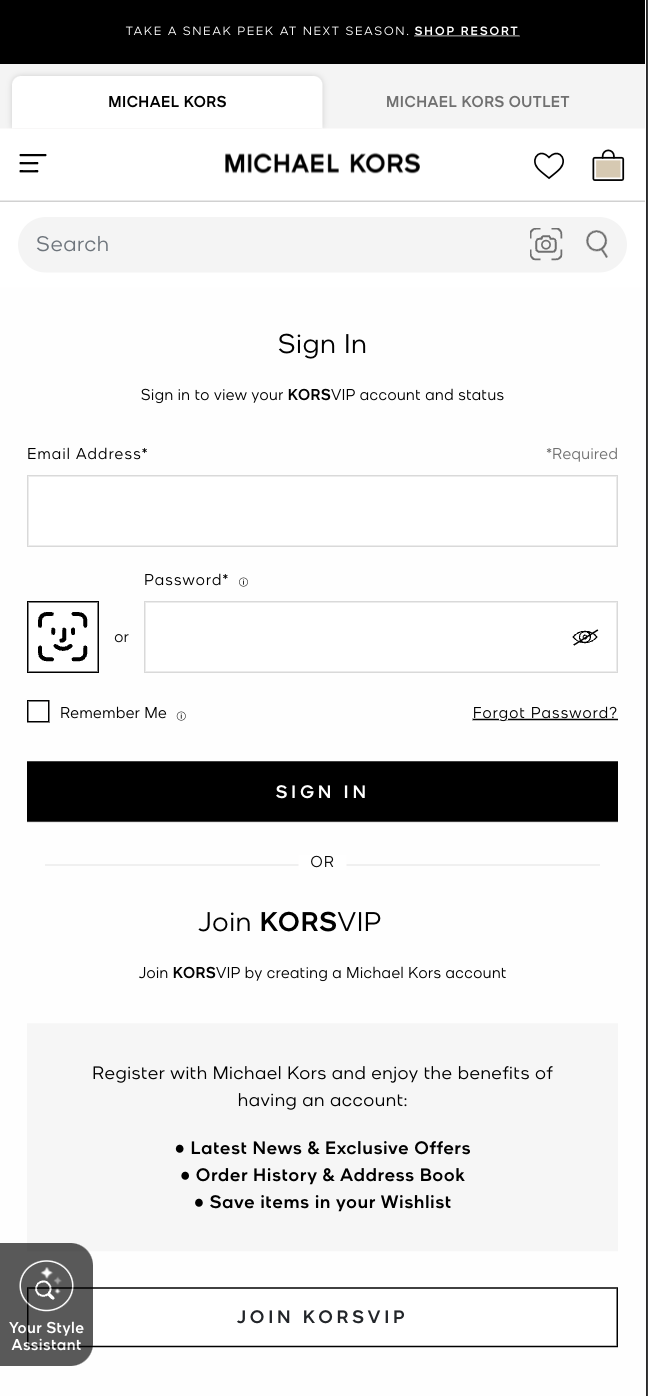
Standalone Button
The OwnID SFCC cartridge doesn’t render automatically this variant.
If you want to use it make sure you enable the configuration option
skipDefaultWidgets, so there’s no overlap with the default (side-by-side) variant. 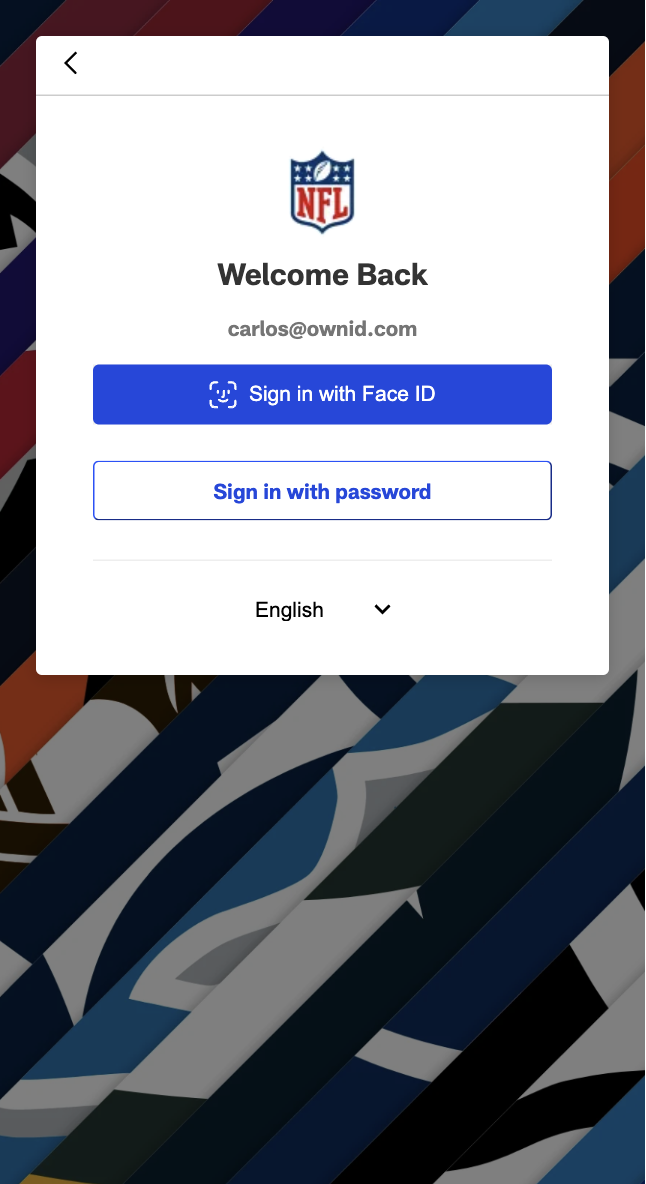
standalone-button variant.
Use the examples below to render the button in your login, register or account recovery pages:
wrapper-div represents the div where the button will be shown. Configure your own.
If you would like to style this button, you can utilize the following CSS variables:
- Finished State (Register)
Cartridge Settings
This section outlines the preferences that can be configured for the OwnID SFCC cartridge.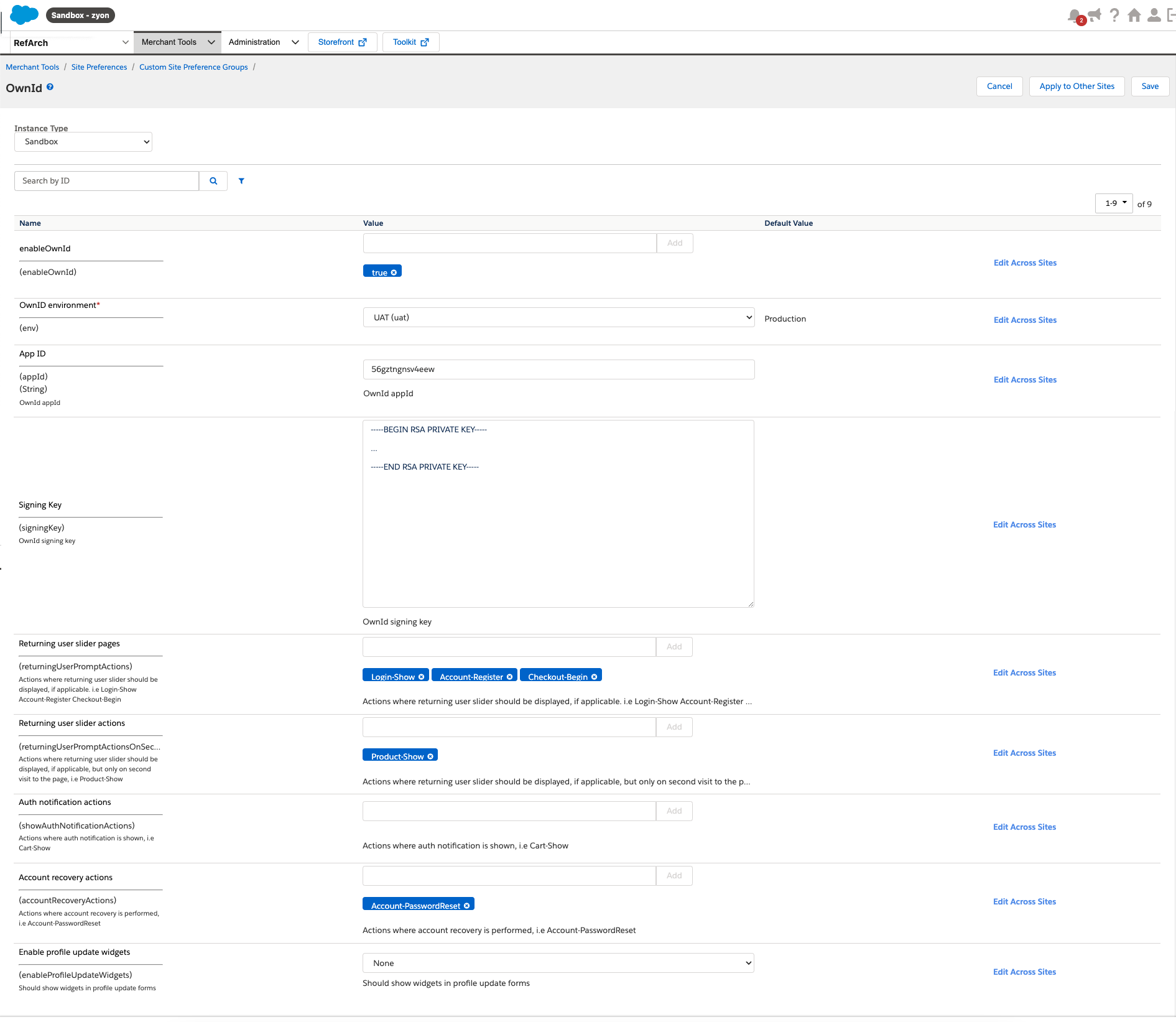
enableOwnId
- Type: Multi-value
- Description: Enables OwnID functionality on specified sites.
- Values:
"true"or"all": Enables OwnID on all sites.- List of locales (e.g.,
"en-US", "en-GB"): Enables OwnID only on specified sites.
env
- Type: String
- Description: Sets the environment for OwnID usage (e.g.,
UAT,Production).
appId
- Type: String
- Description: Specifies the OwnID App ID used for integration.
signingKey
- Type: String
- Description: Private key retrieved from the OwnID console for secure communication.
skipDefaultWidgets
- Type: Boolean
- Description: Should the cartridge skip rendering default OwnID widgets automatically.
returningUserPromptActions
- Type: List
- Description: Specifies the action pages on which to prompt the Returning User Prompt (RUP), if applicable.
- Example:
Login-Show,Account-Register,Checkout-Begin
- Example:
returningUserPromptActionsOnSecondVisit
- Type: List
- Description: Specifies the action pages on which to prompt the Returning User Prompt (RUP), but only on a second visit to any page on the list.
showAuthNotificationActions
- Type: List
- Description: Specifies the action pages on which to show an authentication notification.
- Example:
Cart-Show
- Example:
accountRecoveryActions
- Type: List
- Description: Specifies the action pages on which to prompt for account recovery actions.
- Example:
Account-PasswordReset
- Example:
enableProfileUpdateWidgets
- Type: Boolean
- Description: Displays a passwordless widget on account update forms (e.g., email or password update).
All prompts will only be shown if they are applicable based on conditions such as user context (e.g., mobile usage, returning user status).
Next Steps
Ready to deploy?
YES!
Take me to the Deployment Checklist